FileSure Defend Features
Explore the comprehensive security features that make FileSure Defend the ideal solution for protecting your organization's sensitive data and legacy systems
Advanced Rules Engine
Powerful & Flexible Rule Creation
FileSure Defend's advanced rules engine allows you to create highly targeted policies that control file access based on multiple criteria. Create broad rules covering general conditions or narrow rules targeting specific scenarios, all with "include" and "exclude" capabilities for maximum flexibility.
Rules can be based on a wide range of criteria including:
- File Operations - Control read, write, create, delete, rename, and security setting changes
- File Location - Define rules for network drives, local drives, USB devices, CD/DVDs, and driveless (VSS) locations
- File Characteristics - Apply rules based on file type, filename, file signature, and folder name
- User Context - Create rules specific to username, group membership, program name, and machine name
- Time Restrictions - Apply rules based on time of day, day of week, and date ranges
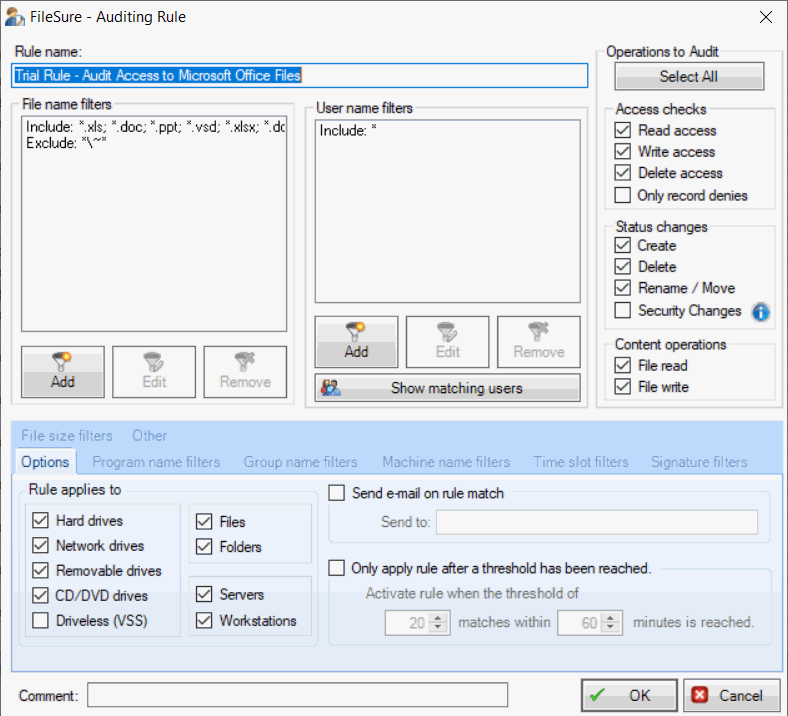
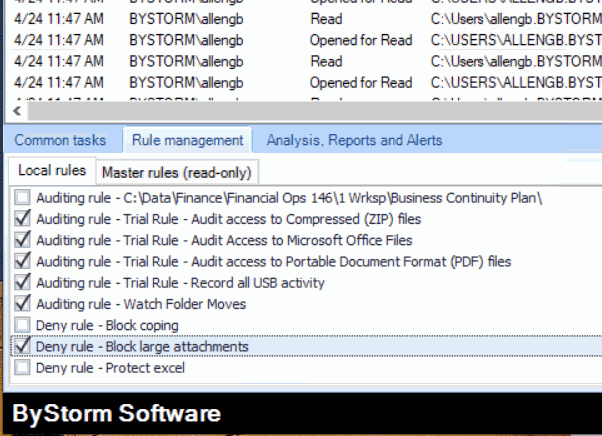
Rule Creation Examples
FileSure makes it easy to create powerful rules that offer protection without interfering with legitimate operations. Here are some examples of how our customers use the rules engine:
Data Loss Prevention
Comprehensive DLP Controls
FileSure Defend offers powerful data loss prevention capabilities by controlling how files can be accessed, copied, and transferred. Unlike traditional DLP solutions that rely on content scanning, FileSure works at the file system level to prevent unauthorized file operations with minimal performance impact.
Our approach allows you to:
- Control Data Copying - Prevent unauthorized copying of files to USB drives, external hard drives, and cloud storage folders
- Block Email Attachments - Detect and block attempts to attach sensitive files to webmail or email clients
- Prevent Cut/Paste - Automatically clear the clipboard when users switch between applications to prevent data exfiltration
- Control "Save As" Operations - Restrict where users can save copies of sensitive documents
- Detect Bulk Operations - Identify and block bulk file transfers that may indicate data theft attempts
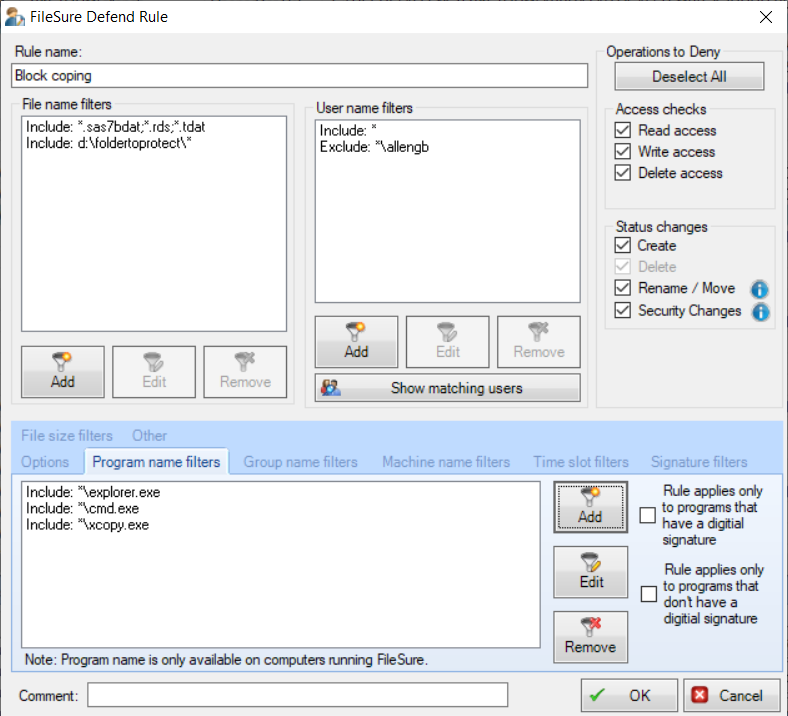
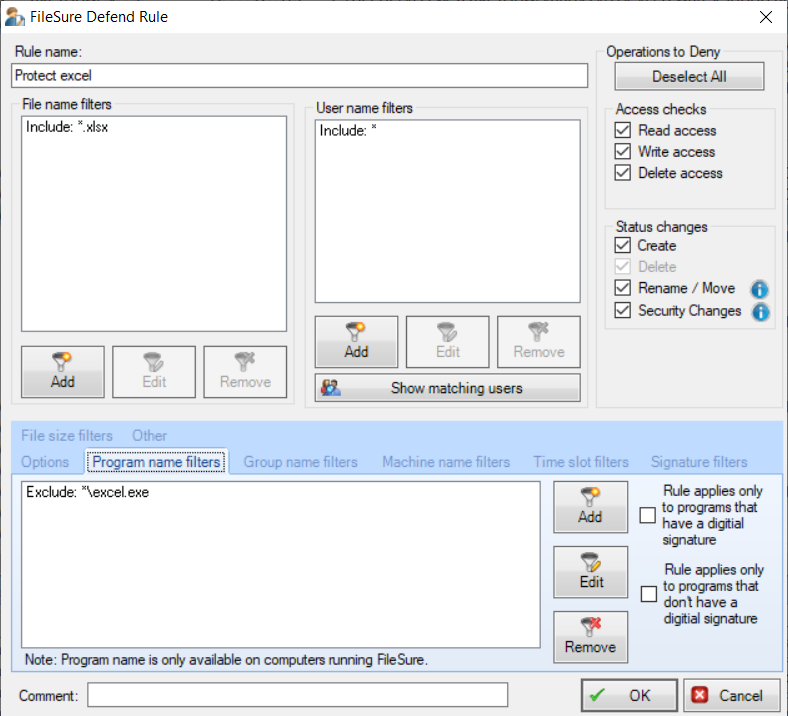
Application-Based DLP Controls
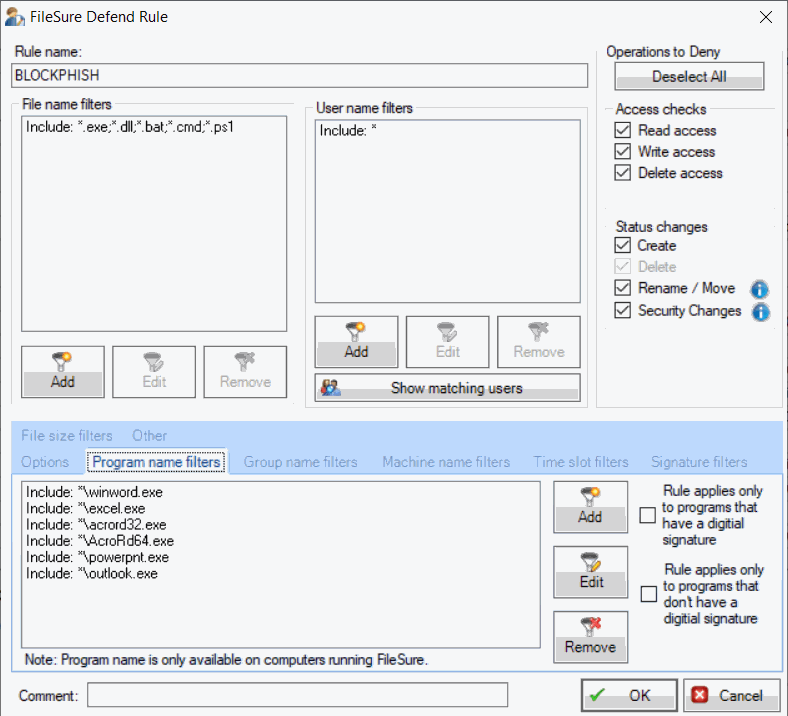
FileSure's unique approach to DLP includes program name filtering, allowing you to control which applications can access specific file types. This application-based control provides another layer of security by ensuring sensitive data can only be accessed through authorized applications.
For example, you can:
- Protect Database Files - Allow only your authorized database application to access database files, preventing unauthorized tools from extracting data
- Secure Document Access - Ensure that only authorized document management applications can access specific file types
- Prevent Data Scraping - Block unauthorized applications from reading files even if users have legitimate access
This application-based control works even if users have full access rights to the files, providing an additional security layer beyond traditional access control lists.
Advanced Malware Protection
Zero-Day Protection for Legacy Systems
FileSure Defend provides powerful malware protection without relying on signature updates, making it ideal for securing legacy systems that can't run modern antivirus solutions. By controlling file operations at the system level, FileSure can prevent malware execution even when traditional security tools fail.
Our approach offers several key advantages:
- Prevent Malware Installation - Block unauthorized executables from being written to protected systems
- Stop File Modification - Prevent malware from modifying system files or configuration settings
- Block Unauthorized Execution - Implement program whitelisting by controlling which applications can be read and executed
- Prevent "Switchblade" Attacks - Block execution of malicious code from USB drives without preventing legitimate use
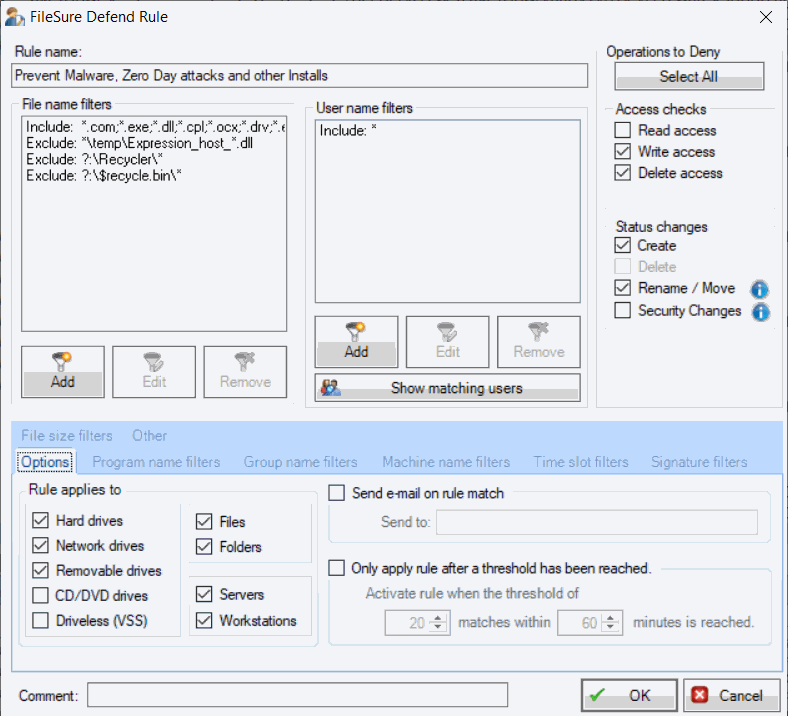
Ransomware Protection
FileSure Defend is particularly effective against ransomware attacks, providing multiple layers of protection to prevent encryption of your critical files. Our solution works on legacy systems where traditional ransomware protection methods may not be available.
- Block program files from being written by applications commonly used in phishing attacks, such as PDF readers and office applications, preventing malware execution.
- Stop commonly exploited applications from modifying your system files, preventing the encryption process that ransomware relies on.
- Detect and block bulk file operations typical of ransomware attacks, stopping encryption before it can affect your entire system.
Centralized Management
Enterprise-Wide Policy Management
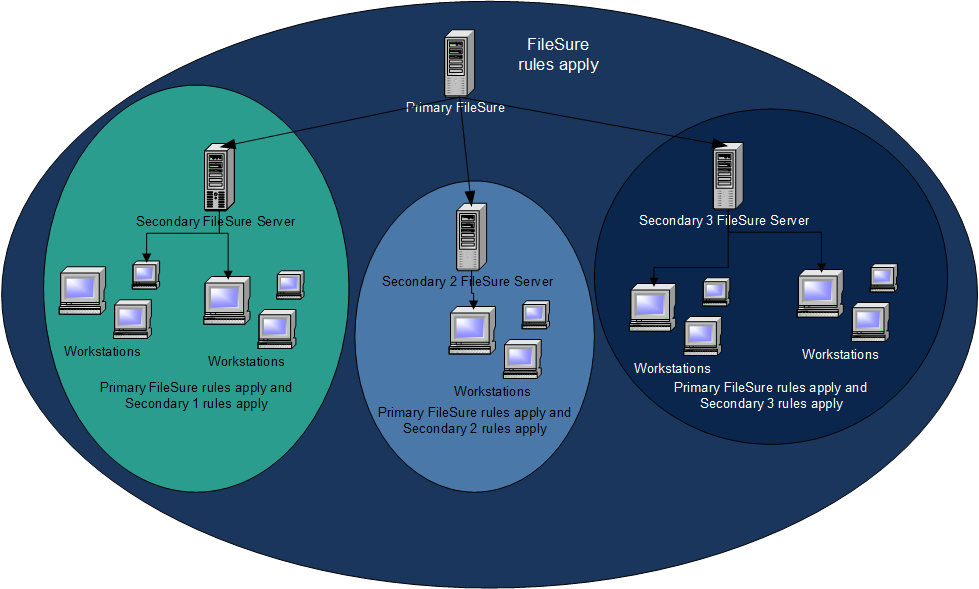
FileSure Defend includes a comprehensive management console that allows you to define, deploy, and monitor security policies across your entire organization from a central location. This centralized approach simplifies security administration while ensuring consistent protection.
Key management capabilities include:
- Hierarchical Rule Management - Define parent and child nodes to create different rule sets for departments or divisions
- Automatic Policy Distribution - Push rules automatically to protected servers and workstations
- Local Override Options - Create local rules that take precedence over master policies when needed
- Offline Protection - Workstations continue enforcing rules when disconnected from the server
- Role-Based Administration - Control who can modify rules and view reports
Workstation Management
FileSure workstation agents operate silently to enforce your security policies while providing centralized visibility into file operations across your organization. The workstation component is designed to be lightweight and unobtrusive while providing robust security.
| Feature | Description |
|---|---|
| Silent Operation | No user interface visible to end users |
| Automatic Updates | Pulls rules from the server every few minutes |
| Offline Protection | Continues enforcing rules when disconnected from the network |
| Local Caching | Keeps local copy of recorded data and pushes to server when connected |
| Reliable Communication | Logs warning in Windows Application Event log if unable to connect to server |
| Scheduled Sync | Retries connection on schedule (default: every 30 minutes) |
Comprehensive Auditing & Reporting
Detailed File Access Auditing
FileSure Defend provides comprehensive auditing of all file operations, giving you complete visibility into who is accessing your data and what they're doing with it. Unlike native Windows auditing, FileSure allows you to target specific activities and filter out noise.
Our auditing capabilities include:
- File Operation Tracking - Monitor reads, writes, creates, deletes, renames, and security changes
- User Activity Monitoring - Track all access by username and group membership
- Program Tracking - See which applications are accessing files
- Privileged User Monitoring - Track access by administrators and privileged accounts
- Session Tracking - Monitor logon/logoff activity and remote control sessions
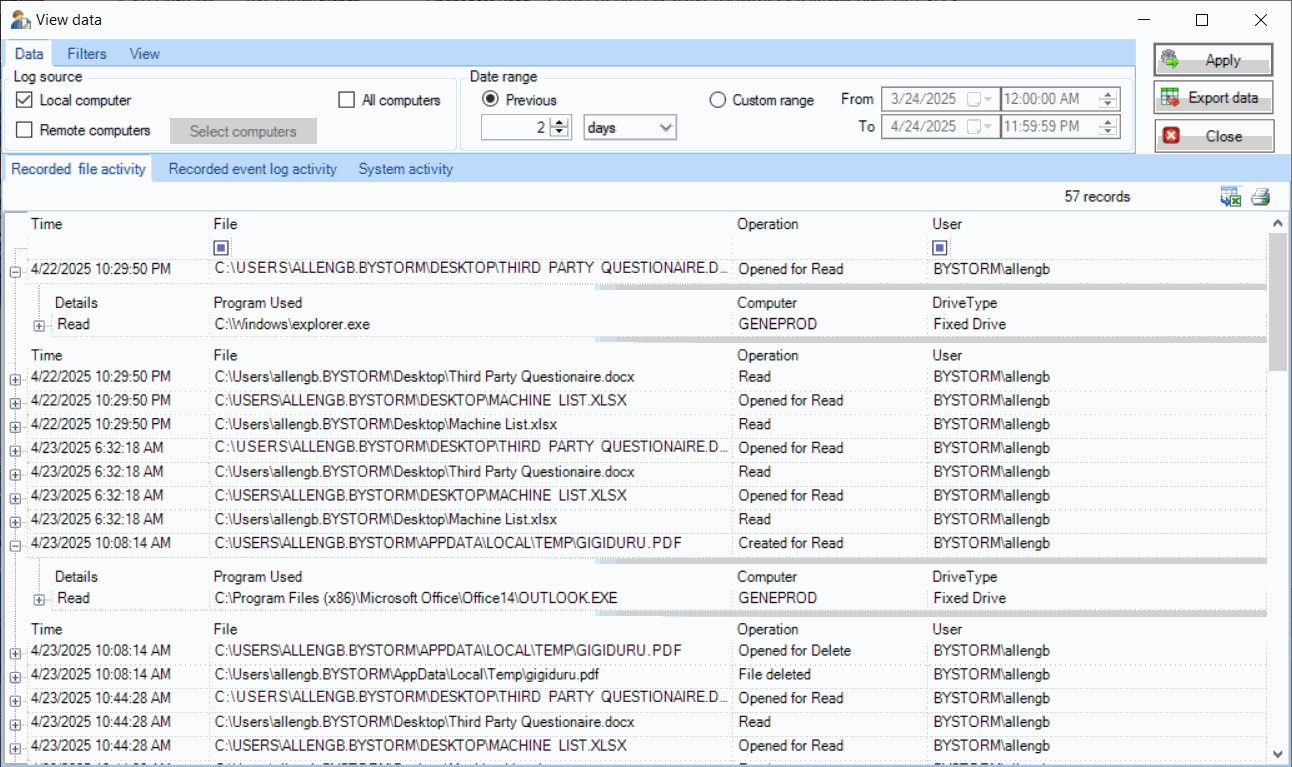
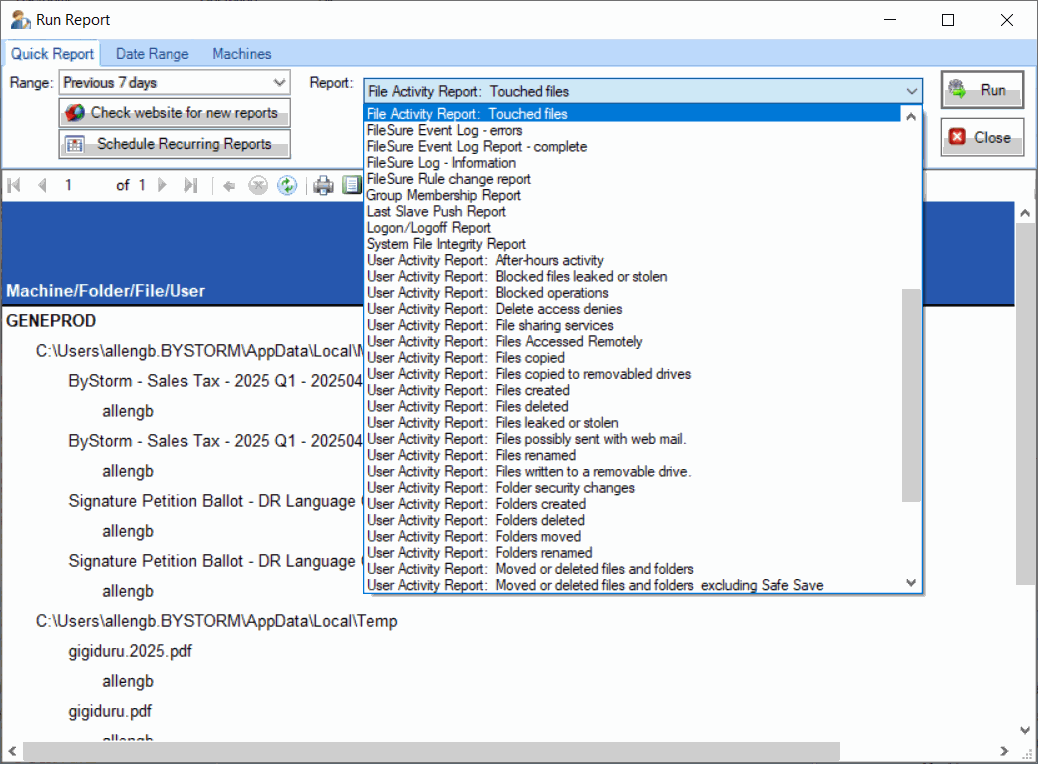
Advanced Reporting Capabilities
FileSure Defend includes powerful reporting tools that help you analyze file activity, identify potential security issues, and demonstrate compliance. With over 50 report templates and customizable query options, you can quickly get the information you need.
- Schedule reports to run automatically and have them emailed or saved to a folder in your preferred format (PDF, XLS, CSV, XML, HTML).
- Apply multiple filtering criteria to isolate exactly the information you need, with flexible options for time periods, users, files, and operations.
- Provide a lightweight interface for non-privileged users like auditors and management to run their own queries without access to FileSure administration.
FileSure's reporting capabilities make it easy to track user behavior, investigate security incidents, and satisfy auditor requests without sifting through massive log files.
Regulatory Compliance Support
Meet Compliance Requirements
FileSure Defend helps organizations meet the requirements of various regulatory standards, including HIPAA, NERC-CIP, PCI DSS, FISMA, FERPA, 21-CFR-11, SOX, and more. Our comprehensive file monitoring and access control capabilities provide the technical controls needed to satisfy auditors.
Key compliance capabilities include:
- File Integrity Monitoring - Ensure files are not improperly modified or replaced
- Access Control - Restrict file access based on job function and need-to-know
- Privileged User Monitoring - Track what administrators are accessing and doing
- Comprehensive Audit Trails - Document who accessed what data and when
- Data Loss Prevention - Control how sensitive data can be accessed and transferred

HIPAA
Healthcare Information
Meet HIPAA Security Rule requirements with technical safeguards that protect electronic protected health information (ePHI) and maintain detailed access logs.
PCI DSS
Payment Card Data
Satisfy PCI DSS requirements for controlling access to cardholder data, monitoring all access, and maintaining file integrity.
FISMA
Federal Information
Support FISMA compliance with robust controls for federal systems, including access restrictions and comprehensive audit logging.
SOX
Financial Records
Meet Sarbanes-Oxley requirements for protecting financial data integrity and maintaining proper controls over information systems.
Flexible Deployment Options
Enterprise Deployment
FileSure Defend is designed for flexible deployment in enterprise environments, supporting both centralized and distributed architectures. The solution can be configured to match your organization's structure and security requirements.
- Central Server Deployment - Install on a central server to manage policies and collect audit data
- Workstation Deployment - Deploy agents to workstations and servers that need protection
- Hierarchical Deployment - Create multiple management servers for large distributed organizations
- Silent Installation - Deploy workstation agents without user interaction
- Group Policy Deployment - Use Group Policy to distribute and manage FileSure agents
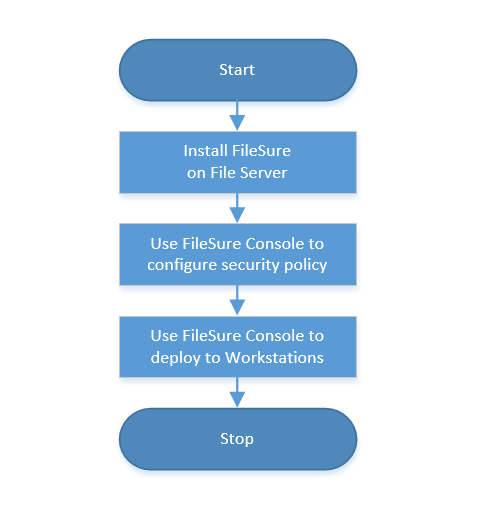
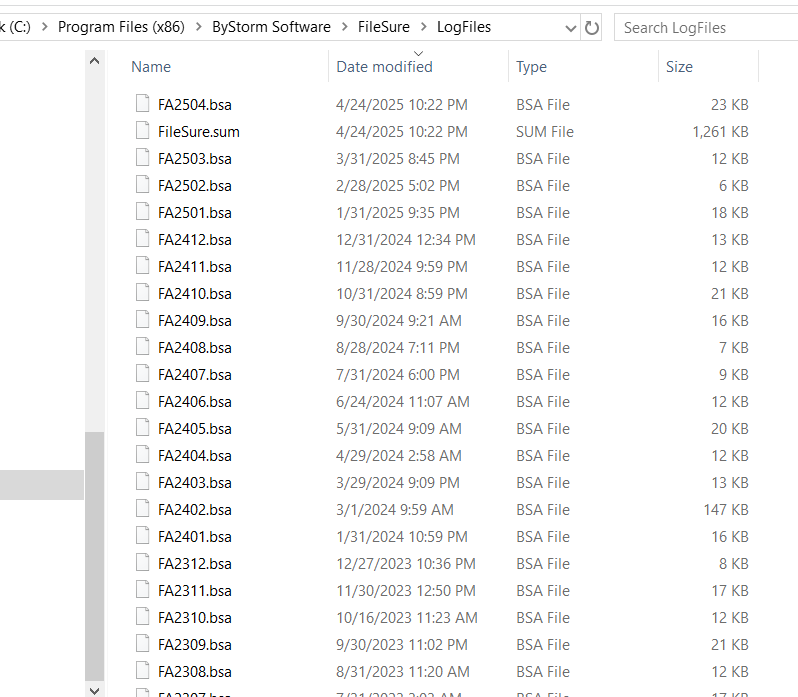
Secure DataStore
FileSure Defend uses a secure, file-based datastore that doesn't require a separate database engine. This approach simplifies deployment while ensuring data integrity and security.
- No Database Required - No need for SQL Server or other database engines
- Encryption and Compression - All data at rest is encrypted and compressed
- Simple Backup - Backup audit data using your existing backup solutions
- Log Archiving - Archive logs to meet retention requirements
- Historical Data Analysis - Search through archived log data by placing files back in the FileSure directory
