Industry-Specific Security Solutions
Specialized file system security to protect your organization's sensitive data, ensure regulatory compliance, and defend against modern threats
Security Solutions for Your Industry
FileSure provides tailored security solutions that address the unique challenges faced by different industries, especially those with legacy Windows systems that can't be easily upgraded or replaced.
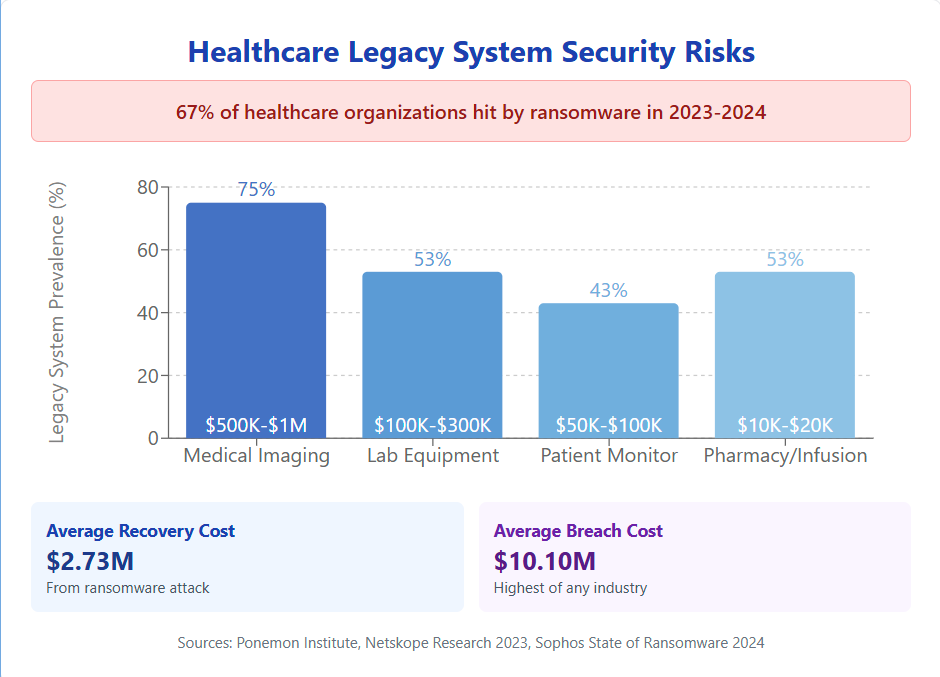
Healthcare Security
Protect patient data, secure legacy medical systems, and ensure HIPAA compliance with FileSure's comprehensive file system security.
- Protect Electronic Health Records (EHR)
- Secure legacy medical applications
- Maintain HIPAA compliance
- Defend against ransomware

Financial Services
Safeguard financial data, protect transaction systems, and meet regulatory requirements with FileSure's advanced security controls.
- Secure customer financial records
- Protect core banking systems
- Meet PCI DSS compliance requirements
- Prevent unauthorized data access

Government & Public Sector
Protect critical infrastructure, secure citizen data, and comply with FISMA requirements using FileSure's file system security.
- Secure citizen data and records
- Protect mission-critical systems
- Meet FISMA compliance requirements
- Defend against advanced threats
Common Security Challenges
Organizations across industries face similar security challenges, especially when maintaining legacy systems that still perform critical functions but lack modern security capabilities.
FileSure's file system security approach provides a powerful layer of protection that works across industries and addresses these common challenges:
- Legacy System Protection
- Secure Windows systems that can't be upgraded or replaced due to compatibility requirements with specialized applications.
- Ransomware Prevention
- Defend against ransomware attacks by preventing unauthorized file modifications, even on systems where traditional antivirus solutions are ineffective.
- Regulatory Compliance
-
- Meet requirements for data protection regulations with comprehensive file auditing, access controls, and detailed reporting.
- Privileged User Monitoring
- Track and control access by administrators and privileged users to prevent insider threats and accidental misconfigurations.

