Detect. Alert. Investigate. Resolve.
FileSure integrates directly into your existing tools and processes, so your team can act quickly and confidently.
-
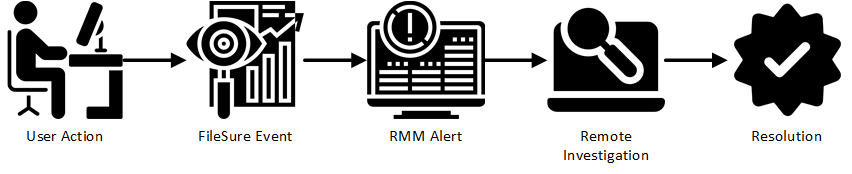
Step-by-Step Workflow:
1. A User Does Something Interesting
- A client employee attempts to:
- Move or delete sensitive files
- Upload documents via webmail or cloud storage
- Copy files to a USB drive
- Run an unauthorized installer or malware
2. FileSure Detects and Logs the Event
- FileSure’s audit and deny rules capture the action in real time.
- A detailed event log entry is generated, including:
- User, file, process, and timestamp.
3. Your RMM System Picks It Up
- FileSure integrates seamlessly with your RMM system (like NinjaOne, Datto, or ConnectWise).
- The event is flagged in your monitoring dashboard as an alert.
- Automated thresholds can also trigger alerts for bulk actions (e.g., mass file copies/deletes).
4. The MSP Administrator Investigates
- Using remote access via your RMM, connect to the client machine.
- Open the FileSure LogViewer to:
- See full context of what happened.
- Quickly identify the user, file, and program involved.
5. Take Action
- Resolve the issue, prevent further risks, or adjust FileSure rules as needed.
- Impress your clients with your proactive security response and detailed reporting.
- A client employee attempts to:
Why MSPs Love This Workflow
- Minimal Disruption – Integrates with tools you already use.
- Proactive Alerts – FileSure ensures you know about risks before they escalate.
- Efficient Investigation – Detailed logs save you time and make root-cause analysis easy.
- Value to Clients – Demonstrate your commitment to file security and compliance.
See How FileSure Fits Your Workflow in Action
- See FileSure in Action
- No credit card required.
- No obligations.
